Get Support
+91 9123517774

Leaf Business Consulting Services
Realizing Real-Time Cloud Transformation
In the ever-evolving landscape of cloud infrastructure, LBCS stands as your partner in unleashing the true potential of real-time solutions. Dive into a realm where promises are not just made but are manifested into tangible outcomes. Explore how our services bring immediacy, efficiency, and resilience to your cloud modernization and management journey.
Leaf Business Consulting Services
Security Optimization for Critical Infrastructure Assets
Critical infrastructure assets face an escalating array of cyber threats, ranging from ransomware attacks to sophisticated espionage. Ensuring the resilience of these assets is not merely a priority; it's a necessity for national security, public safety, and the continuity of essential services.

Our Approach
01. Advanced Threat Detection
Implement state-of-the-art threat detection systems that go beyond signature-based approaches, identifying anomalies and potential threats in real time.
02. Vulnerability Assessments
Conduct regular and comprehensive vulnerability assessments to proactively identify weak points in the security posture of critical assets.
03. Incident Response Planning
Develop robust incident response plans tailored to the unique challenges of critical infrastructure, ensuring swift and effective action in the event of a cyber incident.
04. Continuous Security Monitoring
Utilize advanced monitoring tools to maintain a constant vigil over critical assets, providing real-time insights into potential security breaches.

Leaf Business Consulting Services
Information Security Capabilities for Critical Assets
Critical infrastructure assets hold a treasure trove of sensitive information, making them prime targets for cybercriminals. Protecting this information requires a multifaceted approach that goes beyond traditional security measures.
Our Approach
01. Data Encryption
Implement end-to-end encryption for sensitive data to prevent unauthorized access and safeguard confidentiality.
02. Access Control Mechanisms
Employ robust access controls, ensuring that only authorized personnel can access critical information, minimizing the risk of internal threats.
03. Insider Threat Detection
Deploy advanced tools for detecting insider threats, monitoring user behavior, and identifying anomalous activities that could pose a risk to critical assets.
04. Cybersecurity Training
Conduct regular cybersecurity training programs for personnel handling critical information, fostering a culture of security awareness.

Real-Time Private Cloud Optimization
Our Approach
Dynamic Resource Allocation: Seamlessly adjust resources based on workload demands for continuous optimal performance.
Instant Security Measures: Swiftly implement real-time security protocols to counter emerging threats and vulnerabilities.
Continuous Compliance Monitoring: Monitor and enforce compliance standards in real time, minimizing risks and enhancing data integrity.
Public Cloud Agility in the Blink of an Eye
Our Approach
Automated Scaling: Enable real-time scaling of resources to accommodate changing workloads seamlessly.
Cost-Efficiency on the Fly: Optimize costs dynamically by adjusting resource allocation in real time.
Global Reach at Your Fingertips: Leverage real-time data and analytics for instant global accessibility and performance.


Cloud Migration with Zero Downtime
Our Approach
Live Migration Strategies: Execute cloud migration plans with minimal disruption, ensuring zero or minimal downtime.
Continuous Optimization: Optimize performance and efficiency during and after migration in real time.
Instant Feedback and Reporting: Receive immediate feedback and reporting on migration progress and outcomes.
Cloud Steps: Real-Time Guidance Through Every Phase
Our Approach
Adaptive Roadmaps: Develop adaptive roadmaps that respond in real time to evolving business needs and technological advancements.
Agile Implementation: Execute each phase with agility, adjusting strategies on the fly for optimal results.
Immediate Issue Resolution: Provide instant support and issue resolution to keep your cloud journey on track.
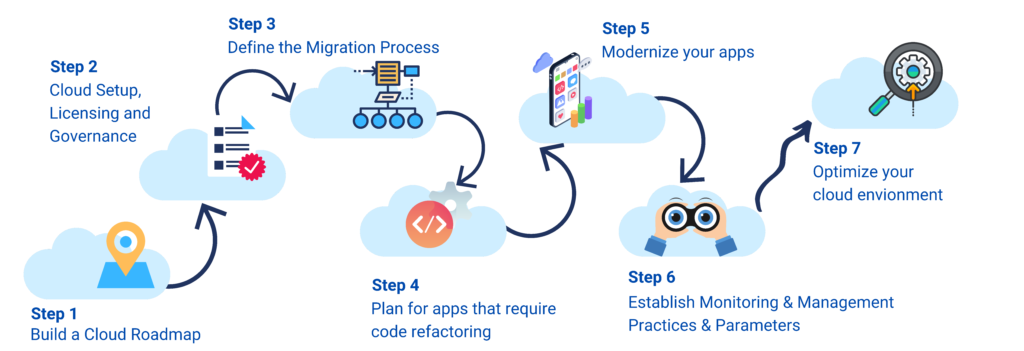

Live Cloud Governance Assurance
Our Approach
Adaptable Policy Frameworks: Establish adaptable policy frameworks that respond in real time to changing business and regulatory landscapes.
Continuous Compliance Audits: Conduct real-time compliance audits to ensure ongoing adherence to standards.
Proactive Risk Management: Identify and mitigate potential risks in real time to maintain a secure cloud ecosystem.
Instant Cloud Assessment Insights
Our Approach
Live Performance Analysis: Evaluate and address performance issues in real time for immediate efficiency gains.
On-the-Fly Security Enhancements: Identify security gaps and propose real-time enhancements to fortify your cloud environment.
Cost Optimization Recommendations: Deliver cost optimization strategies based on real-time spending patterns.


Multi-Cloud Harmony in Real Time
Our Approach
Unified Dashboard: Access a unified dashboard in real time for centralized visibility into multi-cloud resources.
Automated Resource Optimization: Optimize resource usage across diverse cloud platforms in real time.
Instant Threat Response: Implement immediate threat response mechanisms to neutralize potential risks.
Dynamic Cloud Economics Strategies
Our Approach
Continuous Cost Analysis: Analyze cloud spending patterns in real time, identifying areas for immediate cost optimization.
Strategic Use of Reserved Instances: Provide real-time advice on leveraging reserved instances and pricing models for cost reduction.
Budget Management Dynamics: Implement real-time budgeting strategies for effective control and forecasting.


Cloud Finops in Action
Our Approach
Live Workshops and Collaboration: Facilitate live workshops between finance and operations teams for continuous collaboration.
Real-Time Financial Insights: Offer immediate insights into cloud spending and resource utilization for informed financial decisions.
Ongoing Optimization Strategies: Develop and implement real-time optimization strategies for sustained cost-effectiveness.


